Services
Cyber Assessment Assistance
Guidance through complex forms, insurance questionnaires, and audit prep.
Struggling to complete cyber insurance forms, audit checklists, or client-supplied security questionnaires? We help you interpret what’s being asked—and ensure your answers reflect both accuracy and compliance maturity.
- Assistance with cyber insurance questionnaires
- Help completing third-party audit or vendor forms
- Translation of technical questions into plain language
- Gap analysis and risk flagging before submission

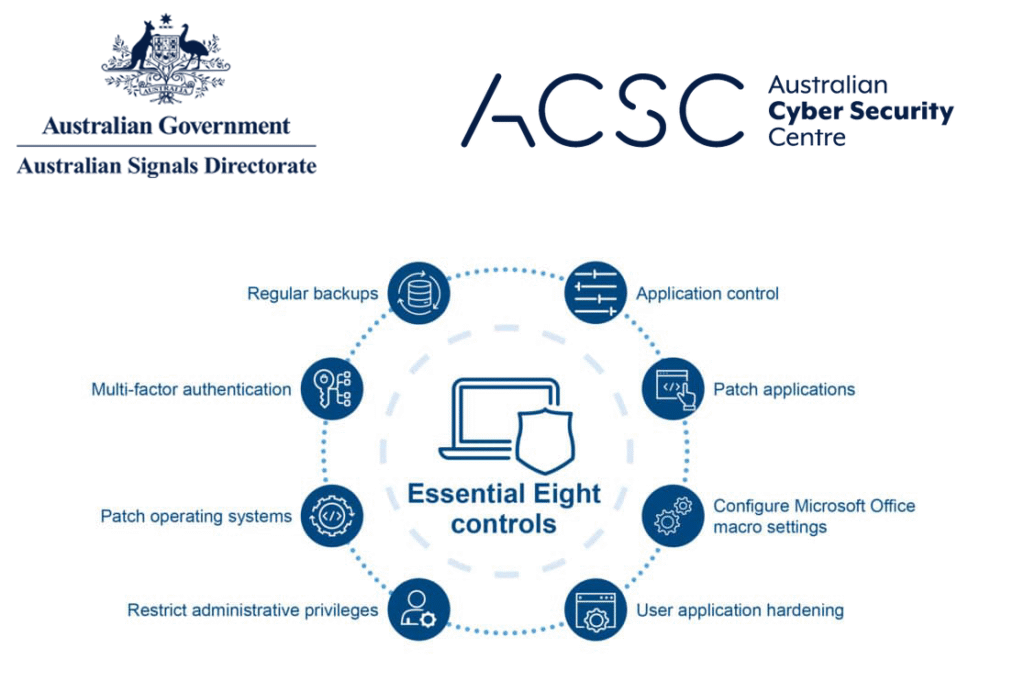
ACSC Essential 8 Readiness
Assess and align your business to the Australian Cyber Security Centre’s Essential Eight maturity model.
Whether you’re working toward baseline maturity or aiming higher, we evaluate how your controls stack up against the Essential 8 framework—and deliver a roadmap to close compliance gaps.
- Full Essential 8 maturity assessment
- Tailored reports aligned to ACSC guidance
- Prioritised control improvements
- Suitable for SMBs, government-aligned sectors, and regulated industries
Cyber Essentials (UK) Preparation
Get ready for Cyber Essentials or Cyber Essentials Plus certification with confidence.
We guide UK-based organisations through the Cyber Essentials readiness journey, helping you identify required controls, close key gaps, and prepare for third-party certification.
- Cyber Essentials & CE+ gap assessments
- Policy and control reviews for UK organisations
- Guidance on remediation steps (via trusted partners)
- Executive summary reports for stakeholders


ISO 27001 Readiness & Gap Assessment
Independent gap assessments to help you align with ISO 27001 security and compliance requirements.
From small teams to large enterprises, we assess your readiness for ISO 27001 certification—identifying strengths, weaknesses, and next steps without pressure or sales tactics.- ISO 27001 pre-certification assessments
- Documentation and control reviews
- Roadmap for audit preparedness
- Partner referrals for implementation (if needed)
Company Policies & Procedures Review
Ensure your internal documentation supports compliance and withstands scrutiny.
We review or help you establish security policies, procedures, and internal standards—aligned to frameworks like ISO, Essential 8, and insurance requirements.- Review of existing policy documentation
- Gap identification against compliance frameworks
- Templates and guidance for missing policies
- Written in plain language for real-world use


Penetration Testing - External & Internal Network Risk and Assessments
Pinpoint vulnerabilities inside and outside your network—without overstepping into sales.
We conduct targeted risk assessments of your network environment to identify weak points, insecure configurations, or potential compliance gaps—without performing implementation or remediation.
- External and Internal Penetration Testing
- External attack surface analysis
- Internal vulnerability mapping
- Executive risk report and remediation roadmap
- Partner referrals for technical action
Disaster Recovery & Incident Planning
Plan for the worst—so your business can respond with clarity and recover with confidence.
From cyber incidents to natural disasters, being caught unprepared can cripple operations and erode trust. We work with your leadership team to build, review, or formalise your Business Continuity Plan (BCP), Cyber Incident Response Plan (CIRP), and Disaster Recovery frameworks.
Scope offers assessment and drafting support—and when needed, introduces you to trusted vendors who can help implement, test, and manage these plans as a service.
- Development and review of BCP, CIRP, and DRP documents
- Assistance drafting incident response playbooks
- Alignment to compliance requirements (ISO, ACSC, insurance)
- Introduction to vetted vendors for implementation & live testing
- Optional handover to partners for active ongoing management


